Cognoscenti provides Continuous Configuration Management and a unique “Time Machine” look and feel to configuration management.
Cognoscenti drive the required analytics and data needed to quickly achieve NIST-800-171 compliance. This enables our customers to obtain detailed configuration settings and changes.
The discussion below addresses section 3.4 of the NIST standards.
Cognoscenti, in addition to CCG’s entire suite of cybersecurity software products, known as CheckMate, provides complete coverage beyond NIST or other compliance requirement standards.
What Phen Collects through Cognoscenti
Cognoscenti provide, with the aid of Phen, a list of more than 100 of the most critical systems in the environment. Phen uses this list of systems to set up and configures Cognoscenti.
From the moment the system is operable, Phen applies one or more TCP protocols (i.e., SSH, WMI, HTML, etc.) to any device identified in the software.
- These devices can be OS servers or desktops (i.e., Windows, MacOs, Linux/Unix, etc.), and networking devices (i.e., Cisco IOS, Nexus, Juniper, etc.).
Cognoscenti have the unique ability to configure Printers, Managed Power Devices, or WiFi stations.
Cognoscenti provide a Time Machine view and continuous review of Firewalls and Firewall rules as they change (i.e., Dell Sonic Wall, Cisco ASA, Fortinet, Sidewinder, etc.).
The Configuration Management Time Machine
Cognoscenti provide a fresh, detailed configuration view to pinpoint the specific hardware and software operating on a given system at any point in its history.
Cognoscenti use this data to define a unique Baseline for each device and collect a scheduled Current System State (CSS). This provides a historical timeline of the critically defined system. The collection and followed state include (but are not limited to) users, accesses, permissions, files, software (installed and versions), configurations, etc. This breaks down to a line-by-line adjustment of configurations for how the system runs or how a specific application is set to run, including registry entries on the Windows side, running configuration on the Cisco side, or actual flat files on the Linux/Unix/MacOS side.
Some examples of the detailed reporting are displayed in the images below.
This is the detailed insight required and provided at the click of a button to report changes in the configuration status. This is performed for any data collection within the history of Cognoscenti’s service for the lifetime of a system.
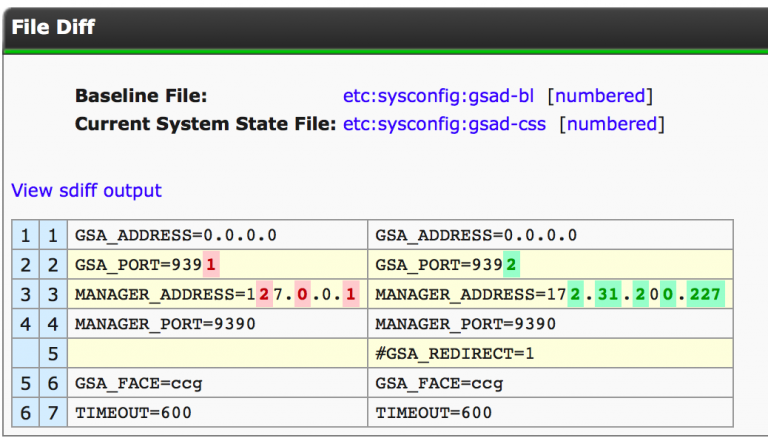
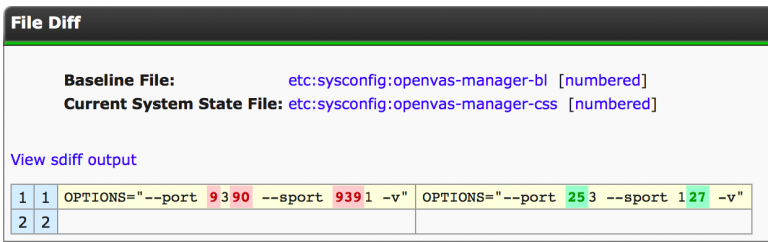
Imagine a situation where an application has a drastic performance change overnight (or more often: ‘it was fine this morning, yesterday, last week’).
- What do you currently have in place?
- What software products are you willing to purchase to provide a detailed analysis down to the specific configuration line of what changed?
CCG’s software can display all application adjustments that occurred over the past week, and in what order those changes occurred. You can track this application for the life of the system being monitored.
Questions Phen and Cognoscenti Can Answer:
- The system was running fine until last week.
- – What changed?
- Government shutdown. 300 Linux and Solaris systems active for 18-24 months shut down. Changes were put in place pre-shut down. Upon system restoration, those changes were lost.
- – What needs to be done?
- The <name any application> was upgraded, but the configurations no longer work.
- – What went wrong?
- The production and test environments are supposed to be identical. They are working differently.
- – What are the inconsistencies in the hardware, software, and configuration?





